Sun Technologies’ RPA Centre of Excellence (CoE)
- January 17, 2023
- 3:33 pm
- No Comments
- Digital Transformation, RPA services
- digital transformation, qa, qa testing services, quality assurance, rpa coe, scriptless test automation tool, software testing
All-In-One Scriptless Test Automation Solution!

Sun Technologies’ RPA Centre of Excellence (CoE)

Sun Technologies implemented an efficient RPA solution across various insurance processes for a leading insurance company in the Caribbean. Keeping the customer experience and speed as an essential factors in insurance commodities processing (policies and claim processing), the client was looking for a partner to automate their processes. Sun Technologies took forward the project and freed them from the effort-intensive manual workload, and helped them increase their overall productivity of the operations team.

We will help you turn your thoughts in to reality! Get in touch with us!

How enterprises can accelerate legacy modernization?
Many CIOs acknowledge the need for legacy transformation and a move towards an agile, modern system. Outdated software slows down the business to respond to changing market needs and puts them behind their competition. A lengthy update or an upgrade approach would become a bottleneck and risk to the company’s day to day operations. Today enterprises are looking for an agile and quick digital transformation approach that makes the process simple to modify and quick to adapt. They also have to address the training needs within the organization during such modernization efforts.
Few other factors include
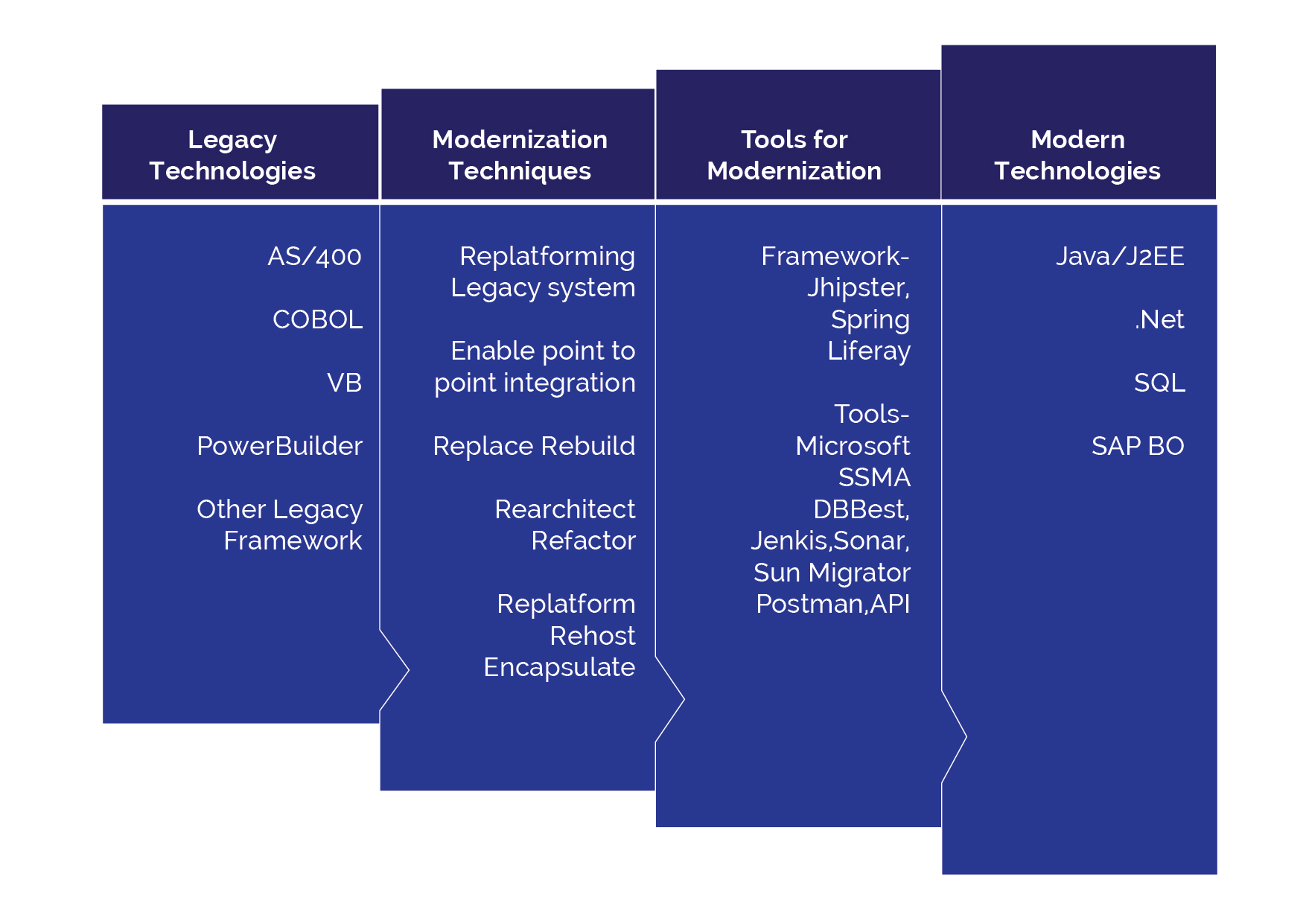
There are many ways to transform legacy systems. Enterprises use their own strategies to achieve legacy modernization. Fully automated migration is an efficient option that uses migration guides, checklist, migration tools and code generators to convert legacy data and code to modernize platforms. It also allows enterprises to tackle legacy modernization without distracting business operations. Refactoring a legacy application reduces the potential risks and enhance IT efficiencies.
Sun Technologies’ unique agile framework enables enterprises to enhance their legacy systems and drive legacy transformation. Our experts build smart workflows for your business processes, make strategic insights, and accelerate your legacy transformation. Our agile framework comprises of a checklist, guide, tools, and framework. The checklist and guide help identify the right approach and provide proper paths to achieve the goal.
There are several approaches towards accelerating modernization; however, at Sun Technologies, we follow an iterative process to accelerate the legacy transformation that reduces risks while providing the agility to meet the dynamic requirements of the business. We start with the evaluation and assessment of the current state of the legacy systems. Our team of solution architects start with impact analysis of various interdependent systems and prioritize the application stack. We decide and prioritize applications that are important and have low impact and risks for modernization. Our code generator reduces the development time significantly, helping businesses to see quick wins and benefits of legacy transformation efforts. We also have a properly layered tech stack where multiple teams can work together.
Post modernization, we have DevOps tools to guarantee there is no data or functionality loss. Our experts ensure that all dependent upstream and downstream systems work seamlessly through detailed data distribution & validation across multiple integration points. From upgrading platform, database, tech stack, Sun Technologies’ solution experts can make it simple and deliver the desired output. We also ensure we develop a roadmap that reduces the complexities while maximizing the benefits of digital transformation, agile development, UI/UX, and quality assurance.
Software modernization is dynamic, requires highly skilled resources, and is risky, irrespective of the chosen method and technique. Yet, the findings are valuable to the risk and gives competitive edge to your business.
“Gartner predicts more than half the global economy turns digital by 2023.”
Our legacy modernization solutions streamline business processes from planning to implementation and provide more value by improving operational efficiency, business agility, and ROI. Sun Technologies helps enterprises accelerate legacy modernization through fast, secure, and state of the art modern technologies and code generators. Get in touch with us today!

With over 18+ years of experience in Software design and development, Tahir's expertise lies in designing and developing high-quality products and solutions spanning multiple domains. He is versatile and always eager to tackle new problems by constantly researching and deploying emerging techniques, technologies, and applications.
Interested in Legacy Mordernization?
We deliver result-driven solutions to boost the competency level and productivity.

Data protection is at risk during this pandemic and likely a target of malicious behavior or intrusive cybercriminals. Data classification offers one of the best ways for enterprises to define and assign relative values to their data and ensures data security The process of data classification enables you to categorize your stored data by sensitivity and business effect, so you realize the risks connected with the data. Instead of handling all data the same way, you can manage your data in ways that reflect its value to your business.
Data exists in three primary states, i.e., at rest, in process, and transit. All three states need distinctive technical solutions for data classification. Also, you should apply the same standards of data classification for each. The confidential data needs to stay confidential when at rest, in process, and transit.
General classification processes for structured data found in spreadsheets and databases are less complicated and time-consuming to manage. Unstructured data that include documents, source code, and email are more complex than structured data. Usually, companies have more unstructured data than structured data.
At Sun Technologies, we believe that one of the best data protection aspects is the right data classification. If you know what and where your critical data is, you would secure it reasonably and save your company from possible heavy penalties and compliance breaches. A little while back, we have seen the GDPR compliance violation at H&M with the largest financial penalty following illegal employee surveillance. The company could have avoided the threat if it had followed privacy compliance policies and addressed the data within data classification plans.
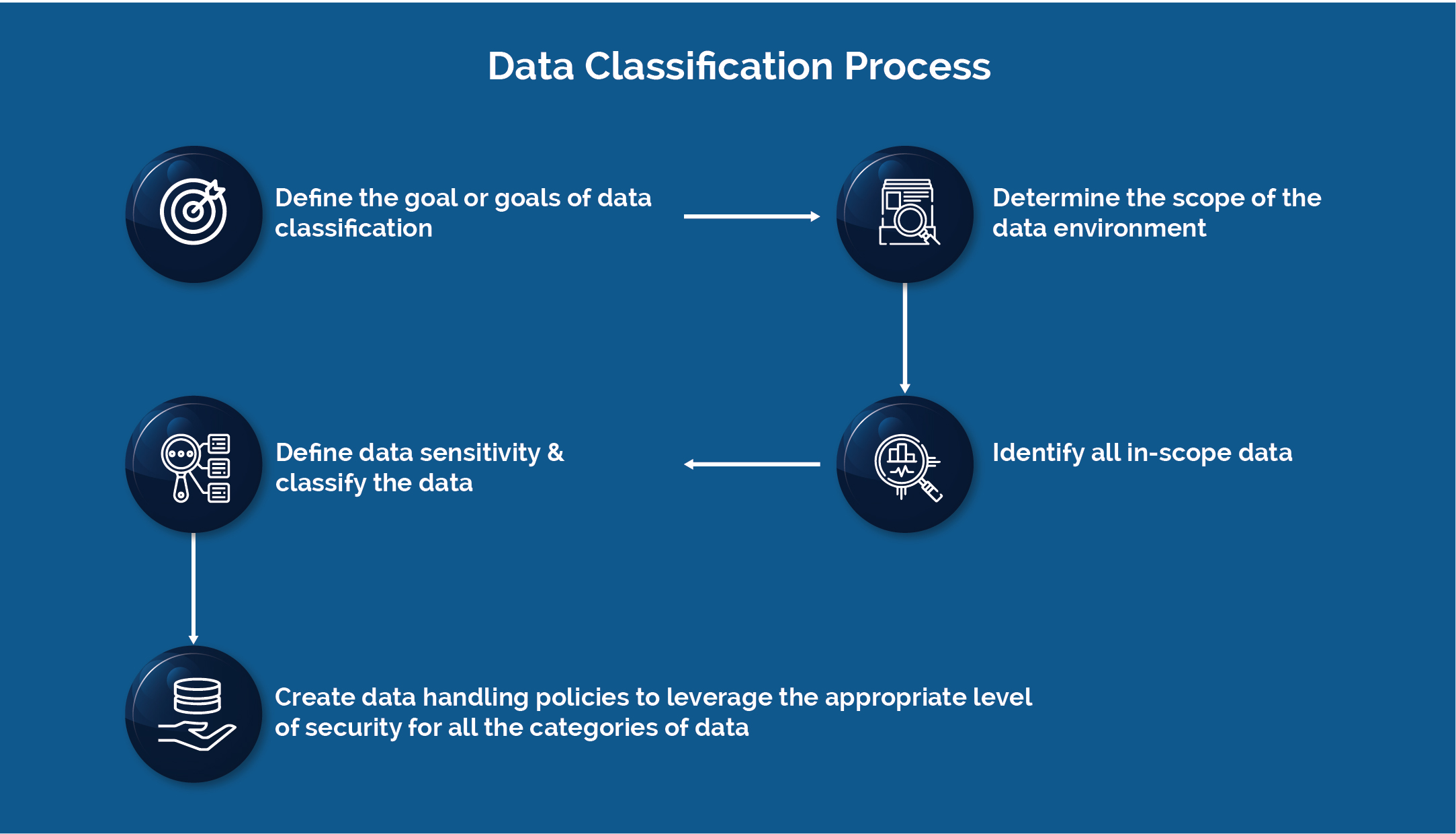

Enterprises can achieve data discovery through various automated tools that are available in the industry. But most importantly, your enterprise should define the classification scheme and criteria initially. At Sun Technologies, we follow the reliable and demonstrated framework to classify, declassify, and secure sensitive data. The following are some of the steps from our extensive framework.
The initial step is to understand the business objectives and evaluate your enterprise’s risk and compliance needs. Then categorize the ranking of risks and a list of initiatives to reduce the risk.
At times, it is challenging to meet the compliance needs to meet the critical business requirements. Thus, a reliable data classification program needs to be developed to classify the data according to its risk and value. We have established a dedicated and demonstrated extensive framework by complying with SOX, NIST, CERT, PCI, PII, HIPAA, and many other regulatory requirements. The scheme is a combination of people, process, innovation, and technology, which will find new data elements, shadow IT, structured and unstructured data. And also, it discovers sensitive data in areas you usually never expect. It will identify the broken process, bad actors, data drift, and declassify the data. With that information, We would suggest implementing a sufficient number of DLP tools to secure data-at-rest, data-in-process, and data-in-transit across the IT industry to deliver comprehensive data security.
Including a proper incident life cycle management to data classification is vital. It reports the incident occurrences and recommends how to respond to that incident, perform the root cause analysis, etc. Sun Technologies has a fully managed SIEM and SOAR capability, which will get the logs and events from your DLP solutions and associate them with external threat intelligence feeds to give environmental and functional alerts through a dashboard. This enables our SOC team to efficiently detect and resolve attacks of all types by providing compliance status, risk profile and categorized incidents that produce the biggest threat to data.
Classifying data helps enterprises ensure regulatory compliance and enhance data security.
Classification is an efficient way to safeguard your valuable data. Identify the types of data you store and discover the location of sensitive data, and this makes you to:
Compliance regulations need enterprises to secure data, such as cardholder information (PCI DSS) or EU residents’ data (GDPR). Classifying data allows you to find the data subject to specific regulations so you can apply them for the required controls and pass audits.
The following defines how data classification can help you meet general compliance standards





Vaidy is an experienced lead Solutions Architect heading sales and project delivery for Cloud (AWS, Azure), DevOps and legacy Modernization projects with a demonstrated history of working in the information technology and services industry. He is a strong engineering professional with a Master of Science (MS) focused in Computer Software Engineering from BITS Pilani. He has the capability to manage bigger teams and generate revenue through new Sales and Account Mining.
Looking for Data Security Services?
We help you to discover best practices and maximize ROI in data security and protection solutions.


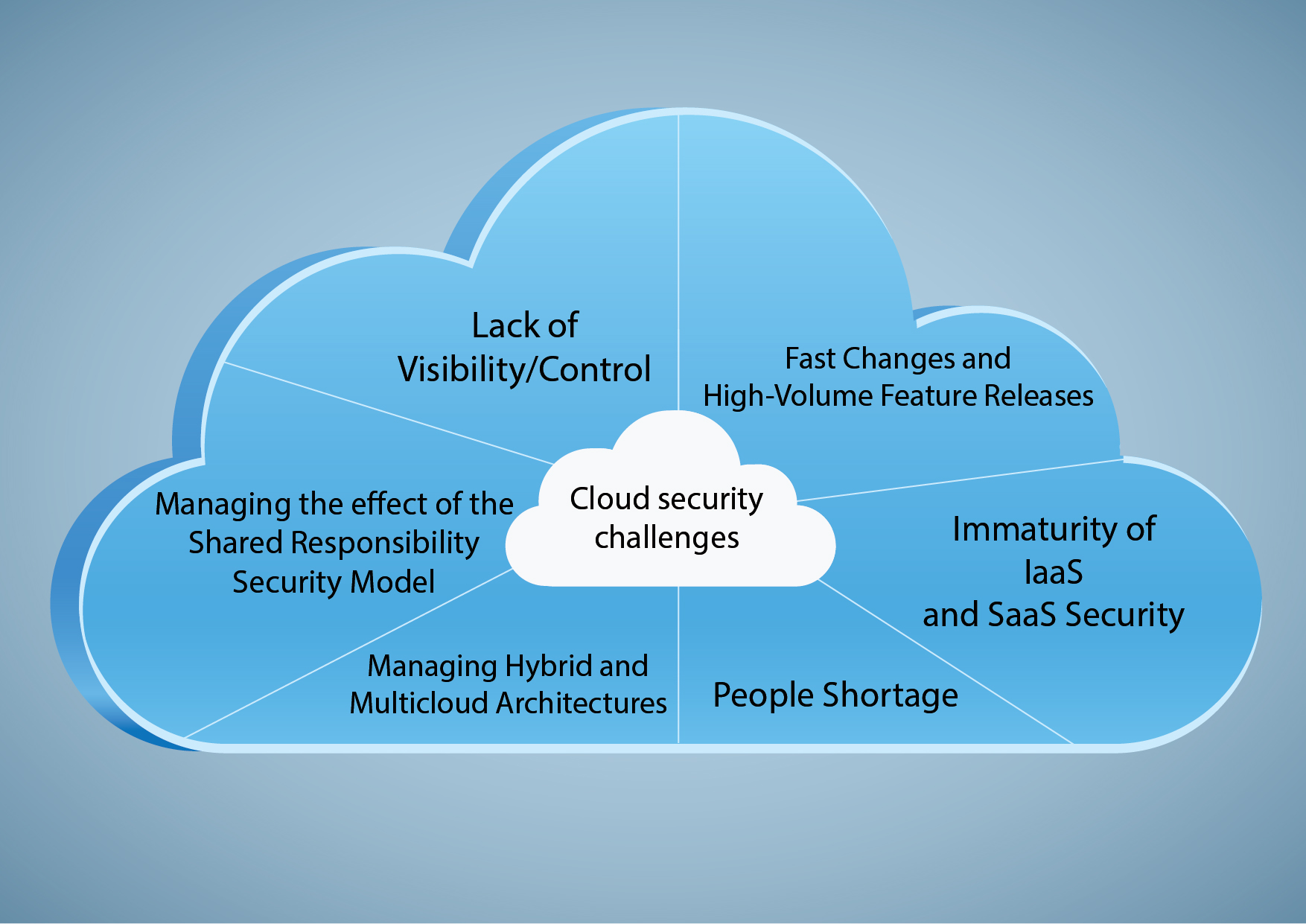
Enterprises are increasingly storing a considerable amount of sensitive data in public clouds. But, initiatives to protect that data lag similar to on-premises efforts. Substantial amounts of critical data are not secured enough. Data security is the most crucial factor to consider.
One of the most significant challenges for enterprises is to make sure the data remains secure and tracked as the data travels throughout the cloud environment. Moving to the cloud changes a company’s attack profile; the surface area increases. By adapting both visibility, to figure out sensitive data and automation to enforce policies, enterprises can better reduce threats.
Consider the following to strengthen your data security in cloud computing.
Categorize your sensitive data
Implement the least privilege model
Audit activity across your environment
Use data masking techniques that include encryption
Make sure your cloud provider provides an SLA that meets your availability needs
These best practices enable you to achieve data integrity, confidentiality, availability, and data security in the cloud.
No wonder the expectations and challenges correlated with securing cloud resident data incorporated a combination of technology, people, and process—with the most significant challenge being employees signing up for cloud applications and services without IT approval.

One of the advantages of using cloud-based technologies is that the user does not have to manage the resources required to keep it working (For example, servers). Yet, handling off the responsibility for managing the up-to-date software, platform, or computing resource can result in less visibility and control over that asset.
The Cloud Service Provider (CSP) is responsible for protecting its network and infrastructure. Their SecOps team observes the computing, storage, and network hardware composing the cloud platform. As a result, the client is responsible for their data and application security, such as patching and access control problems that arise with working in the cloud.
CSPs often introduce new features and solutions to attract new customers and keep current customers from defecting. Few of these changes can have massive effects on SecOps.
CSPs make multiple security tools available in their cloud platforms, including cloud-based IDSs and virtual web application firewalls. However, these CSP security offerings subject to be incomplete compared to their conventional data center counterparts. This gap makes SecOps teams having to install and manage their tools.
Few enterprises are 100% in the public cloud. Many companies have data across public, on-premises, and private cloud architectures, and others have applications and data that bridge AWS, Azure, and Google cloud. Such hybrid cloud architecture builds up tricky security dynamic for SecOps to track. It requires many overlapping and redundant systems for various cloud instances. This increases the possibilities of human error and the need for automation further.
A shortage of proficient, available, and affordable SecOps workforce is becoming an increasingly urgent issue for almost every security enterprise that’s working in the cloud.
The growing use of sanctioned and unsanctioned cloud-based applications with security programs for the cloud that are often less mature than present on-premise initiatives has led to a significant loss of corporate data. The main contributors to data loss included violations of security policy, the implications of employees using their own devices, and the lack of adequate access controls.
Enterprises figured out massive enhancements needed to protect sensitive data regardless of location. And 40% of respondents expect cybersecurity spending to increase considerably.
According to McAfee, the organization’s use of cloud solutions grown by 50% between January and April 2020. Simultaneously, external threat actors increased by 630%. The report also focuses on cloud-native security considerations as critical for company workloads operating in the cloud. In response, some tasks should be automated, such as:
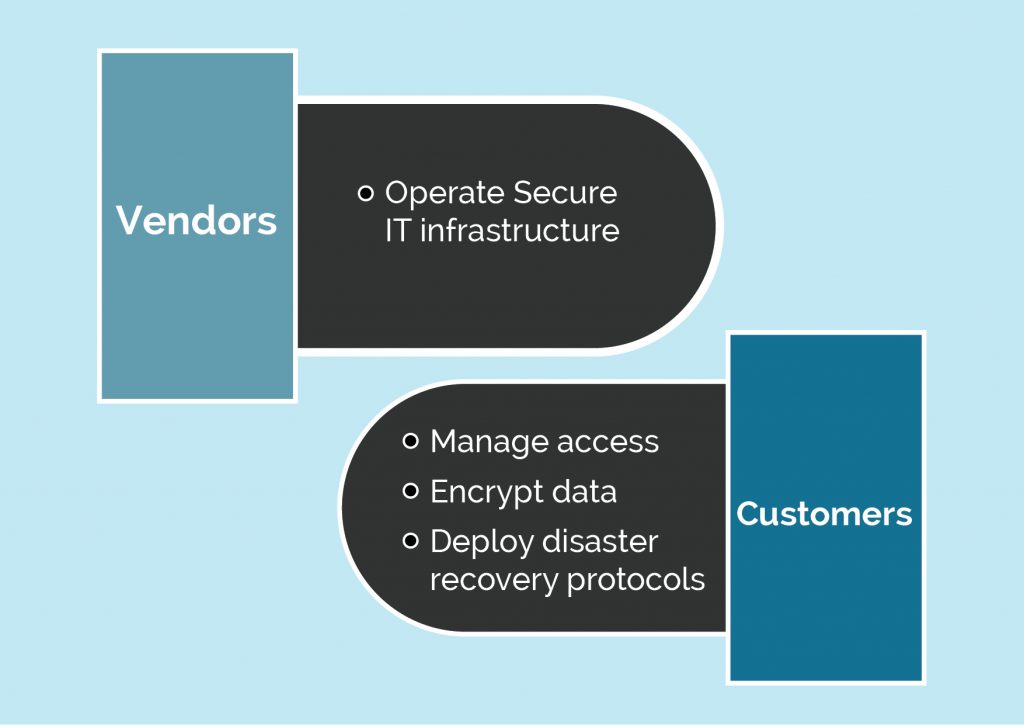
Prediction: Enterprises must carefully realize and follow the shared cloud security responsibility model: vendors are accountable for operating a protected IT infrastructure. Customers are responsible for managing encryption, access, and disaster recovery protocols.

The capability to obtain greater operational efficiencies by unifying security policies across on-premises and cloud-resident data regulate compliance.
Ensuring data confidentiality and data security in the cloud
Ensuring data confidentiality is complex for both maintaining trust in your enterprise and meeting compliance needs. The high-profile breaches consistently in the news highlight the high cost of data security problems. In general, national and international guidelines that include the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR) need enterprises to ensure the security and privacy of various critical data types impose including stiff fines for compliance failures.
The most massive threat to data confidentiality is the capability for unauthorized access to sensitive data. There are two methods for dealing with this risk, which can be used together or individually:
Discover and categorize your data. To ensure the sensitive data is stored only in protected locations and accessible only by authorized users. Also, you need to know which of your information is exposed and the place of the data. Knowing which data needs protection will help you set priorities and apply multiple security controls based on classification outcomes.
Use data masking. This approach involves securing sensitive data by encapsulating it with characters or other data. Data can be hidden in real-time or its original location when requested by an application or a user.
One of the secure and most common data masking approaches is encryption, making it impossible for unauthorized parties to view or realize stored or shared data. Encryption can be asymmetric, which needs a public key and a private key, or symmetric, which utilizes just one private key for encryption and decryption. Actual encryption key management is involved; in general, you must create policies that guarantee only trusted people can access them. Cloud encryption solutions help you to prevent prying eyes from accessing your secured data.
To summarize, while cloud migration can drive your business growth, any compromise in cloud security can push you down. Passwordless methods are popular nowadays, and they ensure safety, as they are used to hold out against cybercriminals, who try to hack passwords for accessing cloud-based apps. One single method or technology won’t protect your cloud data, but a cluster of multiple technologies can surely complement one another. Enterprises invest heavily in the cloud security workforce, i.e., towards skills, competencies, and governance tools. An organization’s own IT department’s role is indispensable as security and privacy have always been two major checkpoints in adopting cloud.




With over 18+ years of experience in Software design and development, Tahir's expertise lies in designing and developing high-quality products and solutions spanning multiple domains. He is versatile and always eager to tackle new problems by constantly researching and deploying emerging techniques, technologies, and applications.
Have a reputable and trustable managed security services provider assess your data storage and security requirements today.


AI and Digital Transformation: 4 Ways to Greater Automation
The initial phase of digital transformation is still an ongoing process for many enterprises, centering around the digitalization of products, services, and business processes. The second phase uses AI to enhance the quality of decision-making, strengthen the relationships with customers, and optimize organizational productivity.
While various enterprises are at various stages of maturity of digital transformation, many companies have already been experimenting with AI separately to discover how it could benefit the business in the second phase of digital transformation.
One of the crucial reasons for the second phase of digital transformation’s unsymmetrical results is the understanding or lack of knowledge of what Artificial Intelligence can do. There has been a general illusion that artificial general intelligence (AGI) can solve any issue when truly artificial narrow intelligence (ANI) is the ultra-modern.
The digital transformation journey has crossed from digitization to digitalization. It also covers different data technologies across various industry verticals. To the extent that data-driven innovations are helping to manifest several advances in digital technologies as actionable, the next boundary in re-molding enterprises is AI transformation. Progression in AI is forcing digital enterprises toward becoming intelligent enterprises. AI technologies are already revolutionizing not just how we recognize and do business, but also the business environment and its’ overall landscape.
Business intelligence is going far beyond dashboards. AI and machine learning are becoming a much more user-friendly process for inexperienced workers as augmented analytics are embedded into platforms.
Organizations are struggling to get their data management and machine learning practices up. This is where augmented analytics are arriving at the rescue. What’s more, it could also help with utilizing machine learning for production purposes, which has been a problem for many enterprises.
The benefits of this have the potential to extend far beyond business intelligence. The passion for implementing AI in enterprises was high at the initial stage. By adding automation to parts of business operations, such as data pipelines and data management, augmented analytics can be one of the elements of the solution to acquiring AI into enterprise production.
Automation has moved past the workforce to white-collar tasks that are repetitive. Just like with some robotic process automation (RPA) tools and chatbots, several automated systems are not necessarily “intelligent” because they are inevitably programmed. i.e., a given input produces a given output. AI enlarges the scope of what automated systems can do and moves enterprises to the second phase of digital transformation.
More than half of organizations acknowledge not having a formal customer engagement program established. Because of this, those organizations had no grasp on the number of customers they’d actually lost in a one year period. On the other hand, most customers expect a consistent experience wherever they engage. Digital transformation using AI can help optimize customer engagement by dynamically aligning the website content with the customer’s preferences.
AI solutions and tools help analyze large datasets in real-time, plan production efficiently, balance supply and demand gaps, schedule factory activities effectively, and develop error-free SCM plans and strategy. AI can also help estimate the market requirement and manage production accordingly to avoid overproduction or shortage of products, either of which would result in loss.
The future of connected digital transformation includes more IoT and industrial IoT devices and the coordination of AI.
IoT and IoT devices are already offering businesses the clarity at the edge, which they lacked before. When combined with AI, the sensors are helping to change the ways companies operate to yield optimization.
Enterprises with and without AI-enabled digital transformation models may adopt some AI by default because it has been embedded in the software tools, applications, and platforms they already utilize. Data scientists should aim to solve complex issues and bring more value from AI in the second phase of digital transformation. Simultaneously, citizen developers (power users) can tackle easier problems, such as optimizing business processes and tasks within their department.





Vaidy is an experienced lead Solutions Architect heading sales and project delivery for Cloud (AWS, Azure), DevOps and legacy Modernization projects with a demonstrated history of working in the information technology and services industry. He is a strong engineering professional with a Master of Science (MS) focused in Computer Software Engineering from BITS Pilani. He has the capability to manage bigger teams and generate revenue through new Sales and Account Mining.


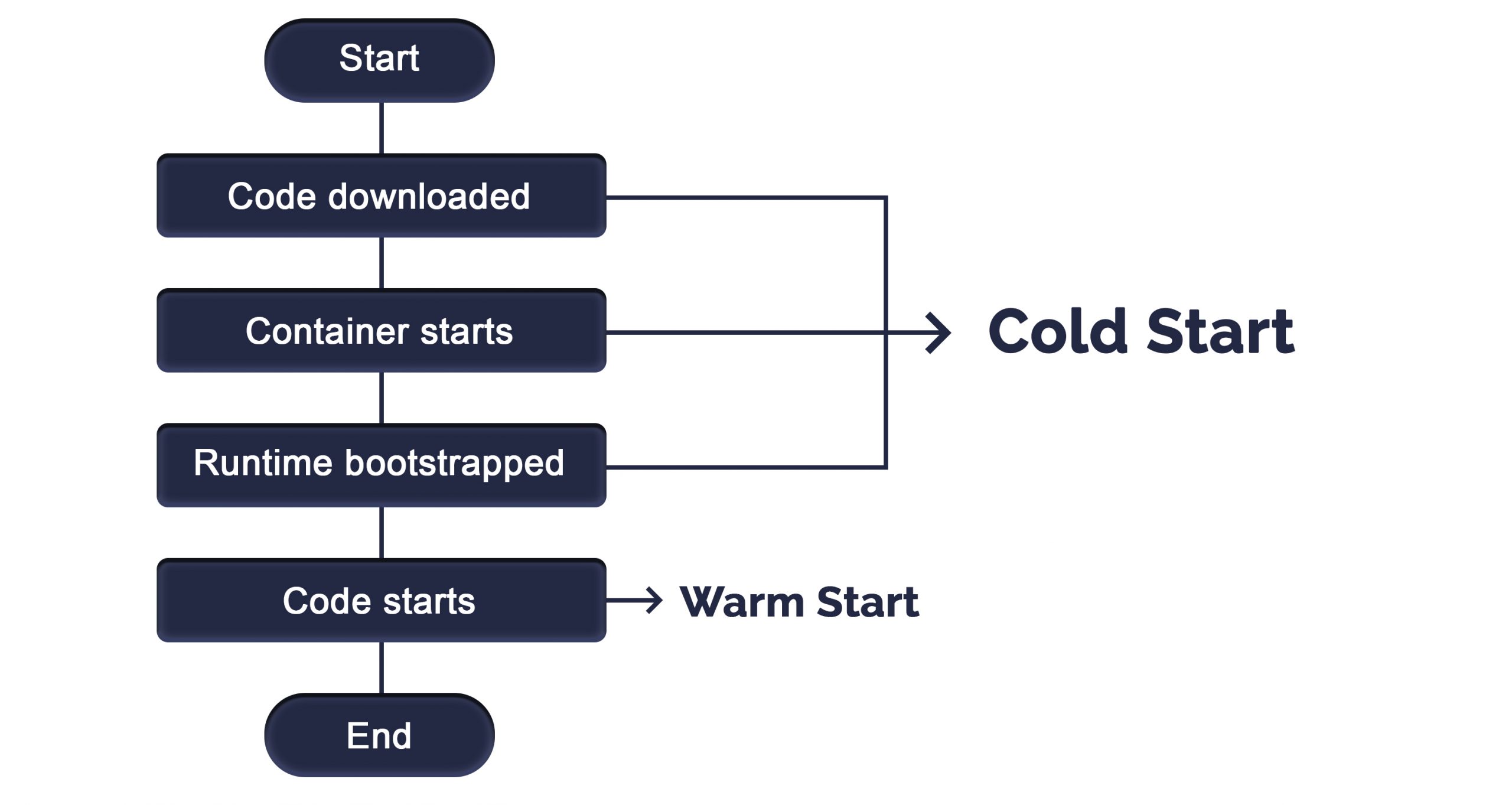
Serverless is a cloud computing deployment model to execute applications by running functions on-demand. The main advantage of serverless is that it allows an application, or part of an application, to be deployed in whenever required. It does not require an always running execution environment. serverless computing is an execution strategy for the cloud. A cloud provider may be google cloud or Aws or Azure, dynamically allocating and charging the user for—only the compute resources and storage required to deploy a specific piece of code.
Thus, serverless execution models can help to save money. Instead of maintaining a server 24/7, companies can deploy code in a serverless environment and pay only for the consumed resources.
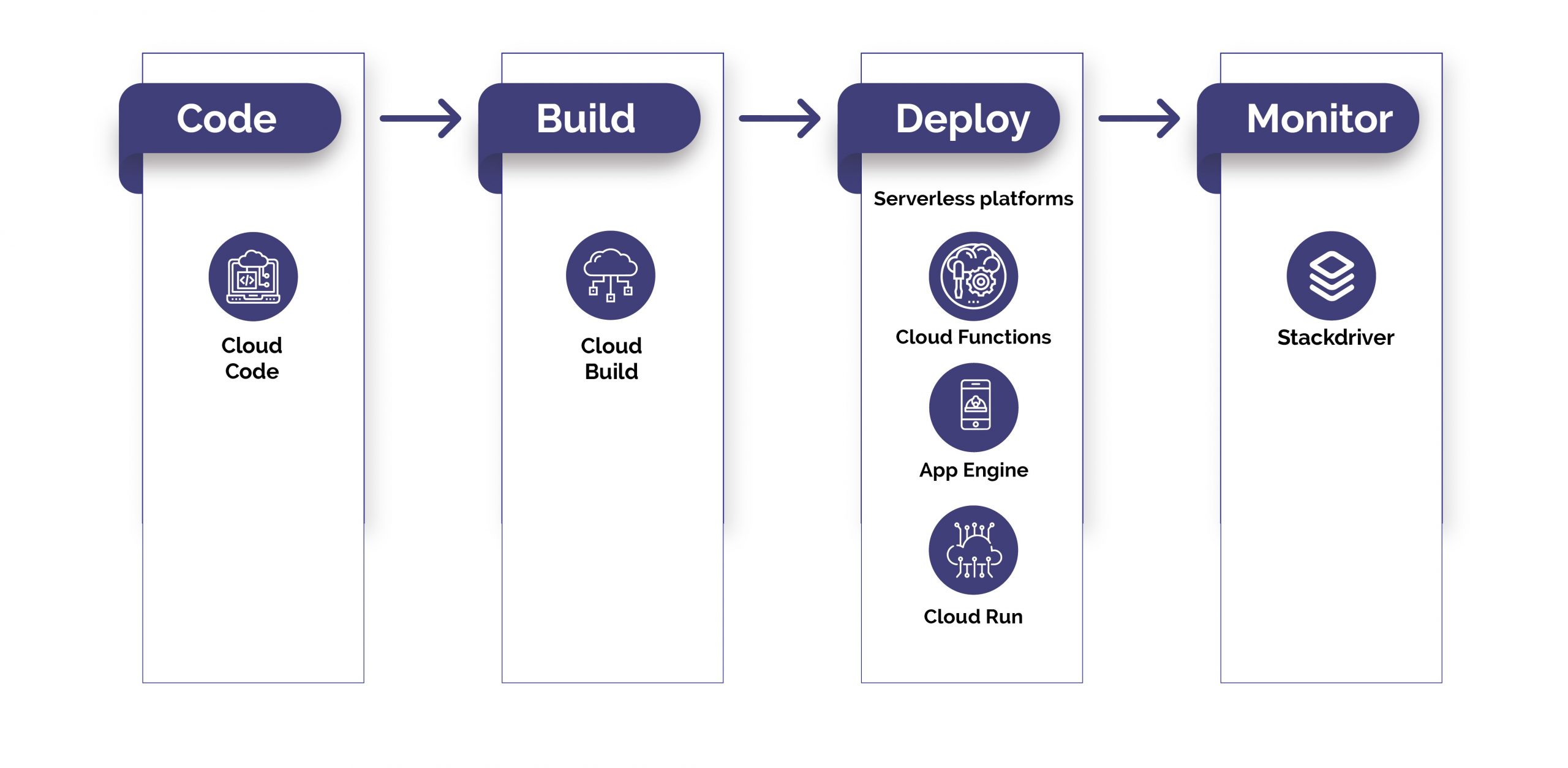

Some of the brand cloud migration consulting providers of IT help in the form of cloud services are Amazon Web Services, Google Cloud, Microsoft Azure, IBM Cloud, etc. Undeniably, there are other best-quality companies in this escalating international mix, with names such as Salesforce, Alibaba, Rackspace, TenCent, Equinix, Oracle, Dell EMC, and other Tier 2 and 3 players. But just because these companies are not in the top four doesn’t mean they won’t be the right choice for your business. Smaller and more professional is what many organizations prefer and search out.
This article will explore three of the top four at a high business level. The effect of the Big 3 in the market, think of them in this prospect:
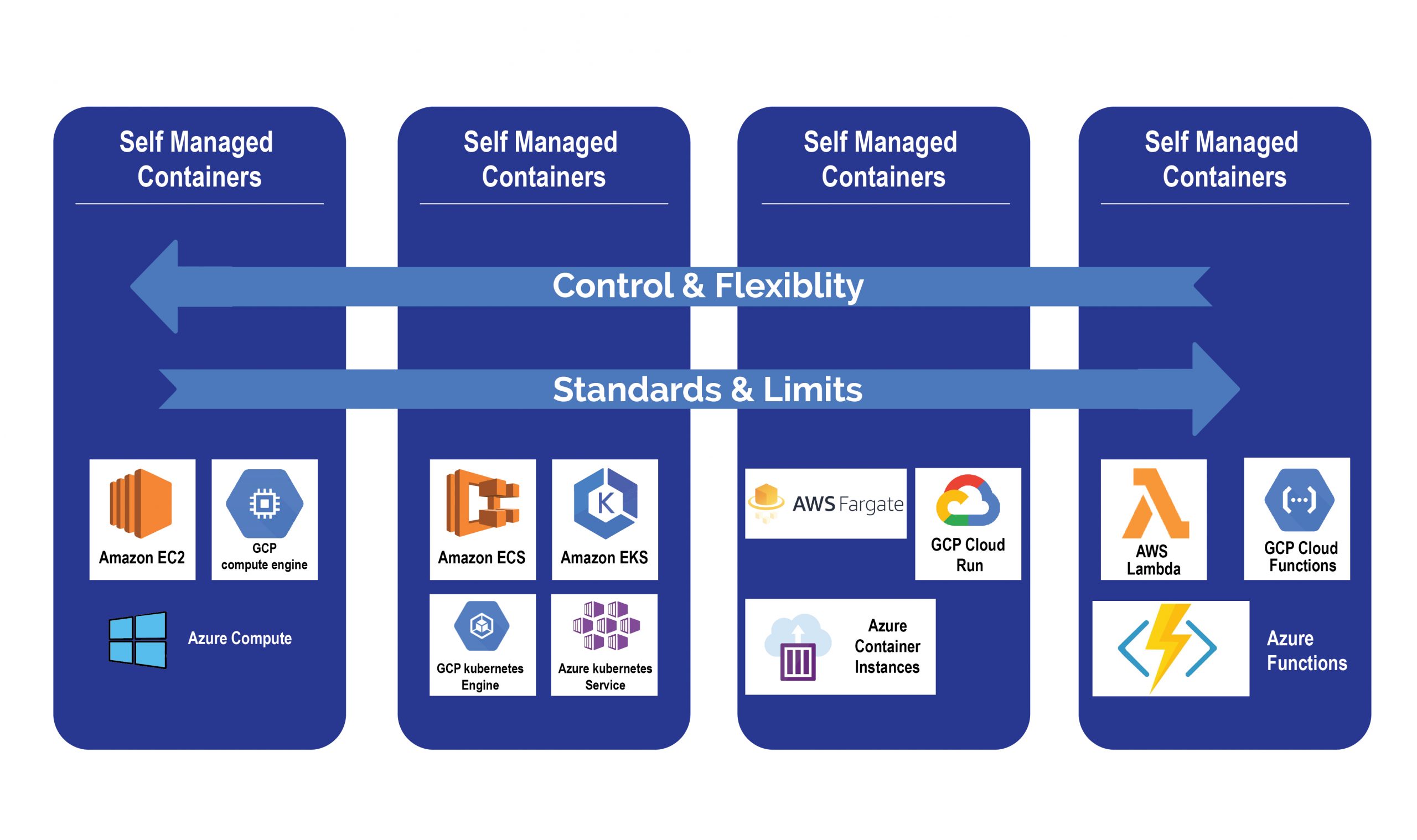
The most crucial factor you have to examine when running container workloads on cloud providers is whether you need to use managed services or commodity services (“do it yourself”).
“Do It Yourself” gives you more control over your container environment’s abilities. The typical cloud services can save time in maintaining the systems, as they are centrally managed and more stable. Altogether using managed services to run container workloads can free up your engineering resources to focus on higher-value work.
There are various options within managed services, such as how much of the infrastructure management you need to control and how much you want the cloud providers to take on for you. Usually, the trade-off is between cost, convenience, and control.
Kubernetes plays a prominent role in the container function space, and all three principal providers deliver a managed Kubernetes service. Initially, it was Google Cloud with Google Kubernetes Engine (GKE) in 2014, followed by Azure with Azure Kubernetes Service (AKS) in 2017, and ultimately AWS followed with Elastic Kubernetes Service (EKS) in 2018. While there are dissimilarities in their details, all of these services are broadly alike in their general contribution.
Each cloud provider also provides a registry service to build and store your container images. Google has Google Container Registry (GCR), Amazon has Elastic Container Registry (ECR), Azure has Azure Container Registry (ACR).

The cloud service platform from Amazon is Amazon Web Services (AWS), which offers services in various domains that include storage, compute, delivery, and other functionalities. AWS helps enterprises to scale and grow. AWS uses these domains in the form of services that can be used to deploy various types of applications in the cloud platform. These services work with each other and yield a productive and scalable result. AWS services are divided into three types:
Amazon launched AWS in 2006. It is the most-purchased cloud platform among existing available cloud platforms. Cloud platforms provide many advantages such as cost minimization, management overhead reduction, and many others.

Azure provides a set of container services that is similar to AWS. AWS Fargate and ECS are Azure Container Instances (ACI), an alternate clustering solution for containerized workloads. The main difference between AWS ECS and ACI is that ACI is sketched from the ground up to run on servers managed by Azure rather than by the users themselves. Ultimately, Azure’s equal to App Mesh is Azure Service Fabric.
Azure is designed and built by Microsoft and launched in 2010. It competes directly with AWS by offering services in domains that include database, developer tools, compute, storage, networking, and other functionality, enabling enterprises to grow their businesses.
Azure services are classified as:
They all can be used by software employees and developers to create, manage, deploy services and applications through the cloud.

Google Cloud is a cloud computing platform. It was developed by Google and launched in 2008 and written in C++, Java, Python, including Ruby. It also offers various services that are IaaS, PaaS, and Serverless platform. Google cloud is classified into different platforms, such as Google Compute Engine, Google Cloud Datastore, Google Big Query, Google Cloud SQL, Google App Engine, and Google Cloud Storage. Google cloud platform offers high-level computing, networking, storage, and databases. It also provides different networking options, such as cloud CDN, virtual private cloud, cloud DNS, load balancing, and other additional features.
Even before Google Cloud emerged, Google was an innovator in container-based services and even containers themselves: Google engineers were incorporated into the introduction of containers to the Linux kernel by introducing groups back in 2006.







Vaidy is an experienced lead Solutions Architect heading sales and project delivery for Cloud (AWS, Azure), DevOps and legacy Modernization projects with a demonstrated history of working in the information technology and services industry. He is a strong engineering professional with a Master of Science (MS) focused in Computer Software Engineering from BITS Pilani. He has the capability to manage bigger teams and generate revenue through new Sales and Account Mining.


Business operations need to be progressively digital to flourish in today’s marketplace. From interactive websites, customer-facing applications, eCommerce, and online marketing models, organizations are quickly executing automated digital technologies.
While there are various approaches you can use to step up your technological game when it comes to how your business operates, embracing an enterprise mobility solution is one of the best methods to bring your business to the forefront of innovative technology while also creating several advantages that any business can benefit from.


Enterprise mobility determines various business elements. Propelled technologies give another life to businesses by reorganizing their operational strategies, improving workers’ efficiency, and generating substantial.
Enterprise mobility management is evolving quickly as a potential answer for entrepreneurs to give their employees a chance to use their mobile devices while working in the field. Business operators can access corporate data or information and get through their duties without the dependency of the physical office, ultimately saving time and expanding the efficiency of business operators.
Enterprise Mobility is about not only managing mobile devices but enabling enterprises to integrate and innovate services more quickly. It helps to boost new opportunities and reduce inefficiencies that slow down business operations. Enterprise Mobility powerfully engages customers to enhance employee connectivity and productivity.

Enterprise mobility solutions are available for organizations of all sizes and across every sector. Many enterprises have long been operating offsite, but haven’t had strategies to do so efficiently. Let us take an example of an architecture of an industry that can benefit from enterprise mobility. The general practice has been to come to the site with hard copies, i.e., paper plans and pencil in hand. Once back in the office or workplace, changes to building specifications are input into architectural CAD software, generating another set of paper portraits to work from.
Architects can complete the same tasks via laptop, smartphone, or tablet with an enterprise mobility solution. Measurements and modifications can be input immediately, and new plans are available instantly. This allows architects to remain agile, competitive, and stand apart from competitors who still operate conventionally.
This kind of technological enhancement would not be possible without the right enterprise mobility development team operating behind the scenes and strategic planning.
As enterprises take their businesses offsite, a world of possibilities opens up. The mobile device management for business improves customer experience, increases productivity, and accelerates advancement, growth, and expansion. With enterprise mobility solutions, companies stay up-to-date as consumer demands for mobility increase.
There are countless benefits to changing the way a company operates and moving from a conventional model to a more active, mobile method of doing business. The following are some of the essential benefits of enterprise mobility.
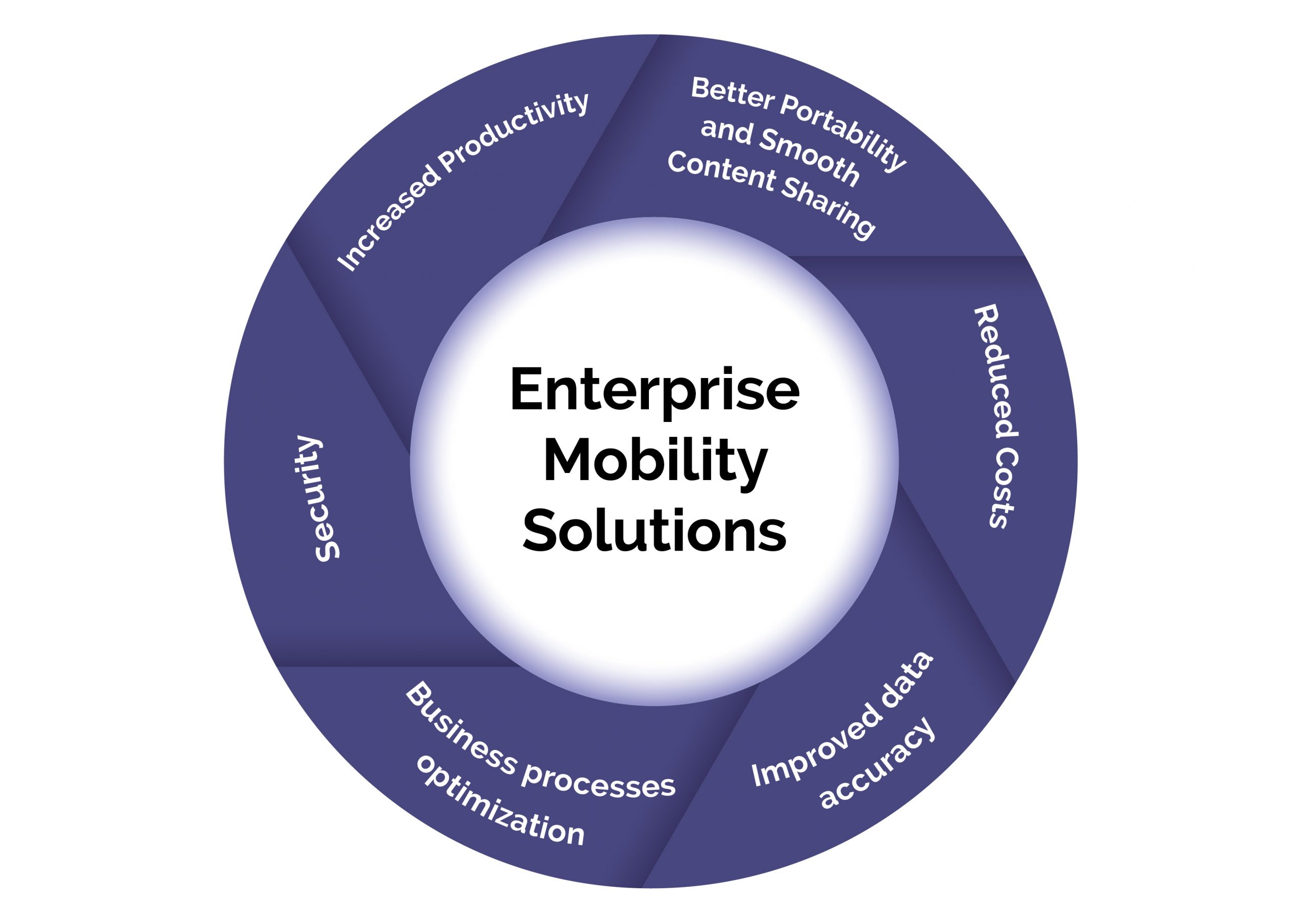

The exposure of enterprise mobility has resulted in a paradigm shift of how business should be managed now and in the future. Business professionals, mobile workers, and field staff can remain just as productive, if not more, outside the office. It delivers workers the resources to use and access data wherever and whenever they need it. The strategic services include cost savings, efficiencies, and new competitive advantage. Sun Technologies can help you understand business outcomes from mobility with a holistic approach. Some of our features include:


DXP (Digital Experience Platform) is a new-generation content management system that marks the customer journey of functions, interactions, behaviors, and locations throughout the complete lifecycle of a purchase.
Based on customer profiles, it enables brands to deliver targeted content and highly-personalized and compelling experiences across a wide range of digital touch points.
Companies use DXPs to build, deploy, and continually improve websites, mobile apps, portals, and other digital experience
Different concepts and technologies behind digital experience platform architecture have emerged with the demands of the digital worker and digital consumer.
The fundamental system to help organizations categorize written content, data, images, and other collateral needed for their online presence.
WEM emerged when digital became a major constituent of brands, new customer channels blown in, and cross-departmental collaboration began to rely on sharing digital data.
The experience swiftly moved beyond just web content. Businesses want to share any type of resource, or group of resources, across any digital touch point – online, in-store, billboards, kiosks, customer portals, eCommerce systems, and more.
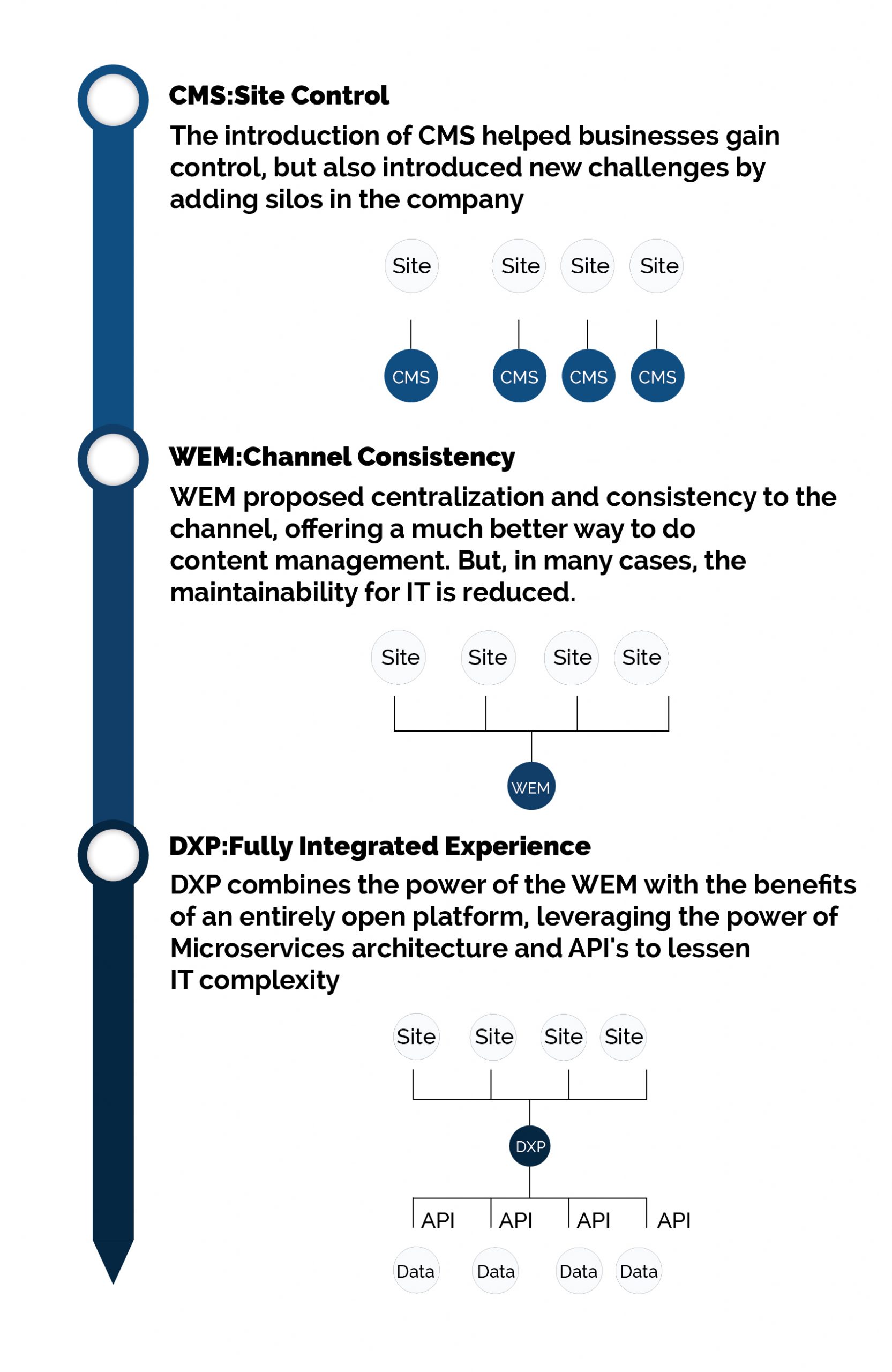

The call for customer experience and relevance has been around for quite some time now in both B2B and B2C. The next generation of top Content Management Systems and Web Experience Management systems transformed websites into an essential part of the customer journey. This gave companies new paths to collect customer data, define personas, and create exceptional experiences with unique content for a wide array of niche audiences. Additionally, it connected new digital channels, such as mobile apps and social media.
The set of factors that are forcing organizations to focus on contextualized digital experiences are:-


Marketers found that these systems are designed to work with native data. Web Experience Management systems are stand-alone marketing tools that are difficult to connect to other systems. Data, profiling, and applying business logic is shortened when you work from a silo. This realization launched the DXP, an open platform that effortlessly combines with other systems and departments. This enables companies to craft truly personal experiences for customers.
Businesses are looking for technology that can offer results, bring forward digitization, and enhance collaboration among various stakeholders. Technology that can integrate their legacy systems and databases while also upgrading portal and migrating to new software is essential. Flawless and well-organized business operations are key for survival in today’s digital age.
The million dollar question remains, is it that difficult to identify a technology that fulfils all of these needs? Well, not anymore. Liferay has provided an Enterprise Solution for organizations to upgrade and migrate their portals. It has excellent features and easy-to-use plug-ins that help deliver an exceptional end-to-end digital experience.
Most of the DXPs in today’s market deliver the same fundamental services. However, the leading DXP providers also provide additional value-adding services on top of those fundamental aspects. Some of the most popular services are: API-integration, omnichannel services, and tools for improved developer experience.
The top providers also have tools for end-to-end omnichannel customer journey mapping and enable the use of “win scores” to prioritize sales opportunities and probability metrics to measure the experience delivered.


Present digital technologies provide various products such as enterprise presentations, digital content management software, search portals, campaign management analytics, etc., which result in data silos. Personalization is generally accomplished through static rule-based configurations in traditional methods. Moreover, the digital transformation of legacy systems involve a custom migration effort for data and content with conventional platforms.
On the other hand, Digital Experience Platforms bring value with a single, integrated platform that has all the needed capabilities including:
All stakeholders, i.e., your customers, business teams, end-users, technology, and operations teams, will benefit from DXP.
WEM is only the start of an organizational DXP. As your CMS tactics mature, you will be able to distribute content to target points outside of your front-end website and add more components of a DXP. The components include mobile devices, web apps, back-office integrations, automated business processes and social networks—all under the protection of compliance and governance.
Sun Technologies makes it easy for developers and marketers to deliver robust, multichannel user experiences. With us, you can produce an architecture that empowers enterprises to digitize workflows, connect various types of customer experiences, and receive valuable and applicable insights. Let’s have a look at how this is accomplished:
Our extensive range of Liferay digital experience consulting solutions at Sun Technologies provide support and guidance for document management, audience tracking and targeting, collaboration, and mobile experience management. You can create a flexible experience for your users using our solutions.




With over 18+ years of experience in Software design and development, Tahir's expertise lies in designing and developing high-quality products and solutions spanning multiple domains. He is versatile and always eager to tackle new problems by constantly researching and deploying emerging techniques, technologies, and applications.
Talk to us about DXP. We’re ready to help accelerate your journey!


Migrating to the cloud is a complex process that must be customized to address the technical, functional, and operational needs of an organization. A successful migration strategy should not only address the short-term aims, such as decreasing hosting costs, but also the long-term goals, like better alignment between IT and business objectives. To meet these goals, organizations tend to focus on three main cloud migration strategies. We’ll explore each below.
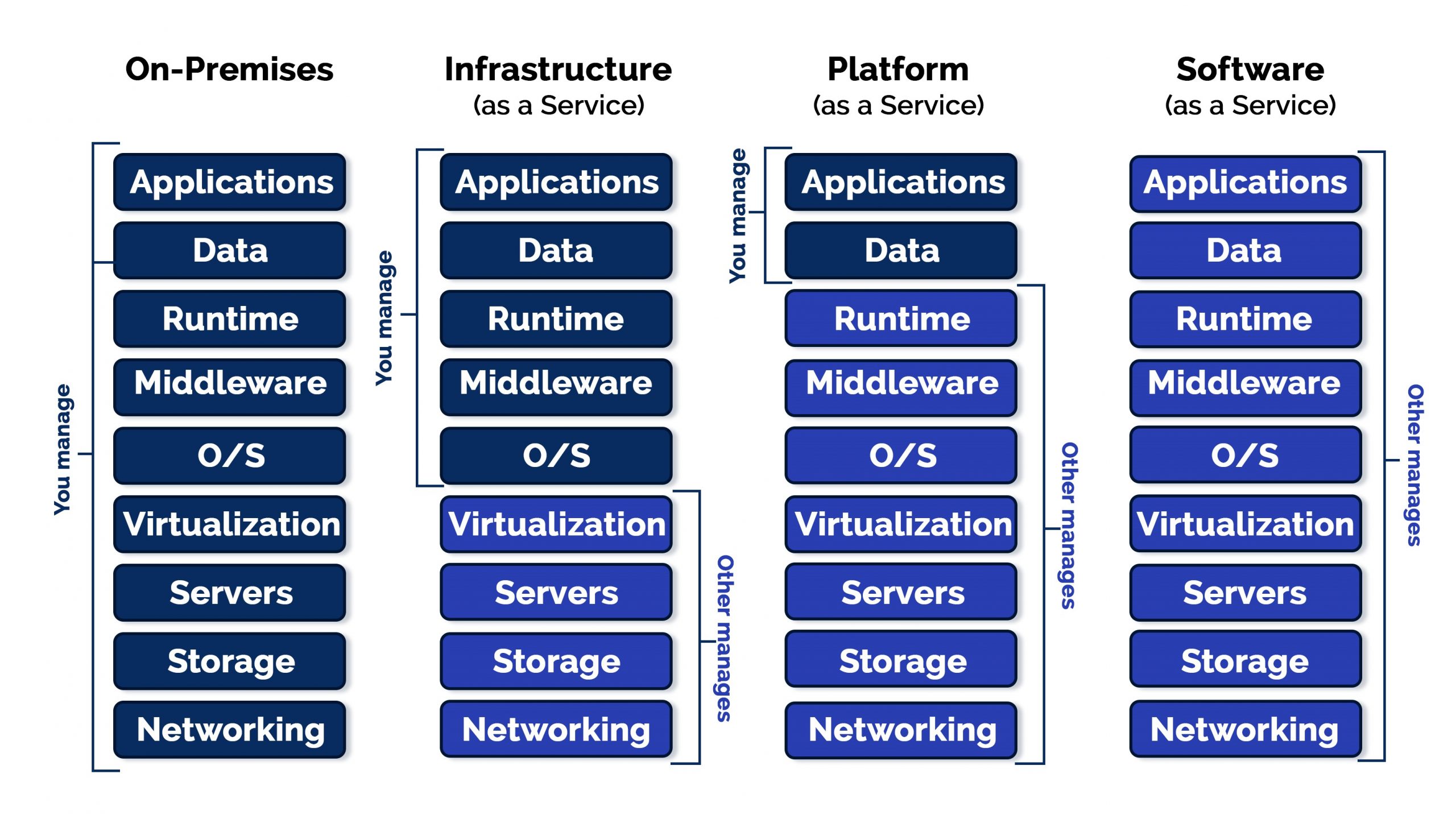
The process, method, and tools for migrating workloads to the cloud are considerably dependent on the aimed cloud migration models: IaaS, PaaS, and SaaS. Let’s have a look at each of these migration approaches.
Among all these options, the simplest and fastest way to get an existing application to the cloud is with a lift-and-shift, Infrastructure-as-a-Service migration
“Lift and Shift” has proven to be a unique approach for many organizations looking for a quick, low-risk method to move their workloads to the cloud. But what if you had an additional option to lift and optimize your primary infrastructure as part of your cloud journey?
Think strategy: Lift–and-shift is one of the approaches to migrating your apps to the cloud, which means moving an application and its correlated data to a cloud platform—without restructuring the application.
There’s no all-purpose transition for moving an application from your on-site data center to the cloud. However, there are accepted core migration paths; many consider lift and shift (re-hosting) to be among them. Life-and-shift provides a way for businesses to secure their investments in business logic, workflow, and data trapped in on-premises hardware.
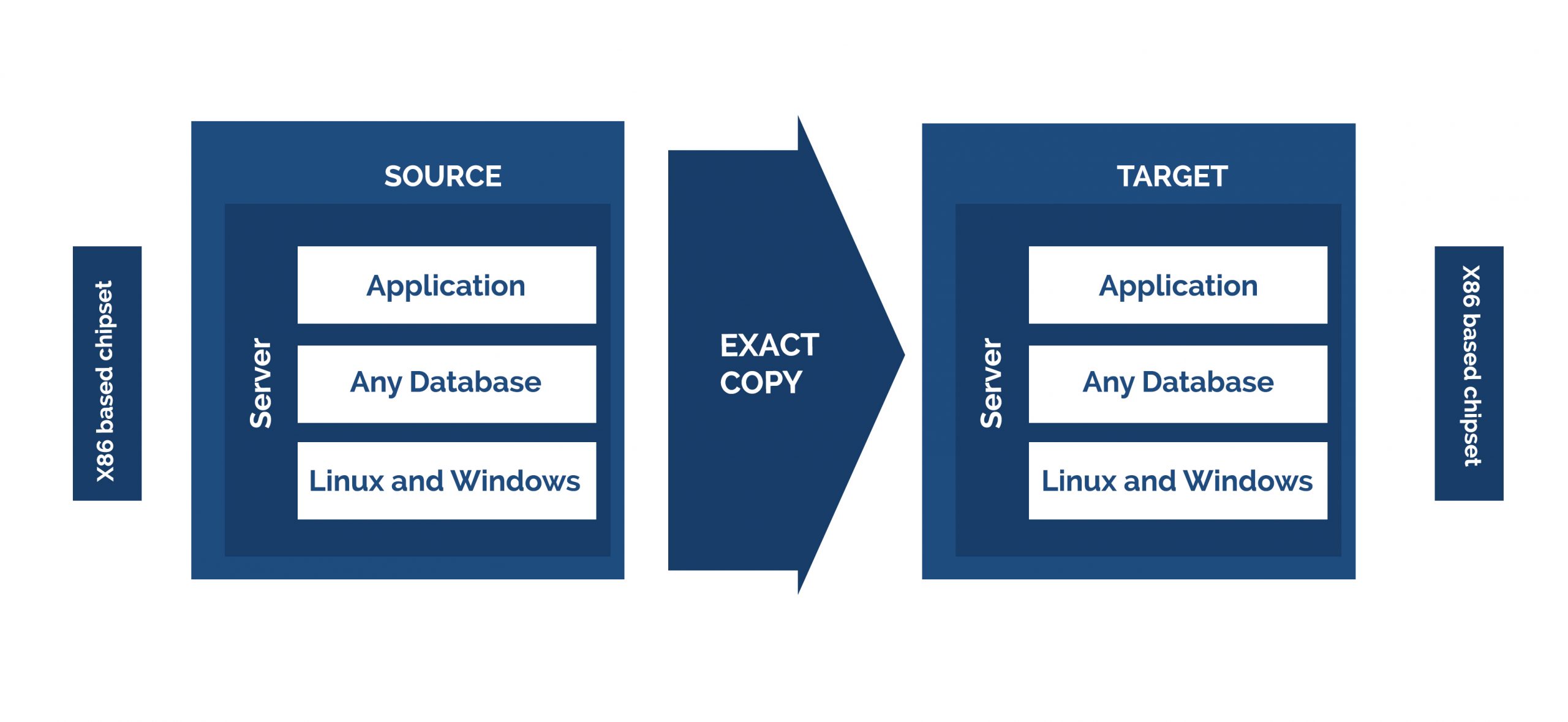

Migrating your application and correlated data to the cloud with less or zero changes is the lift-and-shift migration approach. Applications are expertly “lifted” from the present environment and “shifted” just as it is to new hosting premises, which means in the cloud. There are often no severe alterations to make in the data flow, application architecture, or authentication mechanisms.
The lift-and-shift approach opens ways to IT modernization by moving to open and more expandable architecture in the cloud. Organizations ponder lift-and-shift for solid business reasons such as cost-effectiveness, improved performance, and flexibility.
Nevertheless, one business strategist provides a more organic explanation. He confronts that applications perform and emerge depending on their environments; and that the cloud offers larger size and diversity of services versus on-site data centers.
With the lift-and-shift method, on-premise applications can move to the cloud without remodelling. Since they cannot take full advantage of native-cloud features every time, this may not be the most cost-effective migration path. To avoid bounce back, businesses require a cost-allocation strategy and clear-cut roles within their organization to monitor cloud spending. This will most likely need additional tools.


Let us evaluate some of the principal benefits of using the Lift-and-Shift method:
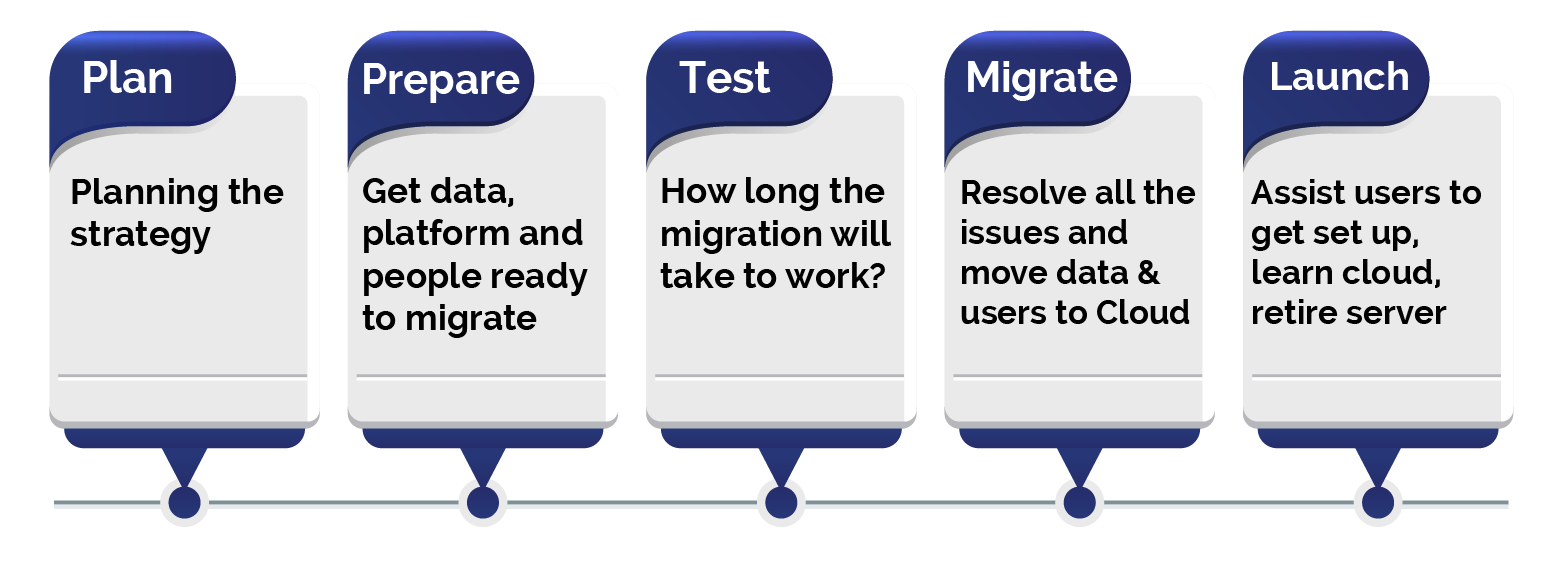

Step 2: Evaluate all the connections in and out of the application and its data.
Ultimately, we would always advise working with a provider who has expertise in migrating applications. Sun Technologies can help you decide what the right method of migration is for your organization,, offer guidelines for the future of your application, and ensure that this is all hitched in with your broader cloud strategy.
Take a look at how our clients have benefited from our transformational method to cloud migration with the below capabilities:
You require a cloud migration provider to traverse costs and technical complexities. Sun Technologies is one of the secure, fast, automated cloud onboarding solution companies with governed migration services. It also strengthens APIs to mirror existing server environments and move them into private, public, or hybrid clouds without interrupting existing workload functions and performances.





Vaidy is an experienced lead Solutions Architect heading sales and project delivery for Cloud (AWS, Azure), DevOps and legacy Modernization projects with a demonstrated history of working in the information technology and services industry. He is a strong engineering professional with a Master of Science (MS) focused in Computer Software Engineering from BITS Pilani. He has the capability to manage bigger teams and generate revenue through new Sales and Account Mining.