
All-In-One Scriptless Test Automation Solution!
All-In-One Scriptless Test Automation Solution!
Enterprises are increasingly storing a considerable amount of sensitive data in public clouds. But, initiatives to protect that data lag similar to on-premises efforts. Substantial amounts of critical data are not secured enough. Data security is the most crucial factor to consider.
One of the most significant challenges for enterprises is to make sure the data remains secure and tracked as the data travels throughout the cloud environment. Moving to the cloud changes a company’s attack profile; the surface area increases. By adapting both visibility, to figure out sensitive data and automation to enforce policies, enterprises can better reduce threats.
Consider the following to strengthen your data security in cloud computing.
Categorize your sensitive data
Implement the least privilege model
Audit activity across your environment
Use data masking techniques that include encryption
Make sure your cloud provider provides an SLA that meets your availability needs
These best practices enable you to achieve data integrity, confidentiality, availability, and data security in the cloud.
No wonder the expectations and challenges correlated with securing cloud resident data incorporated a combination of technology, people, and process—with the most significant challenge being employees signing up for cloud applications and services without IT approval.
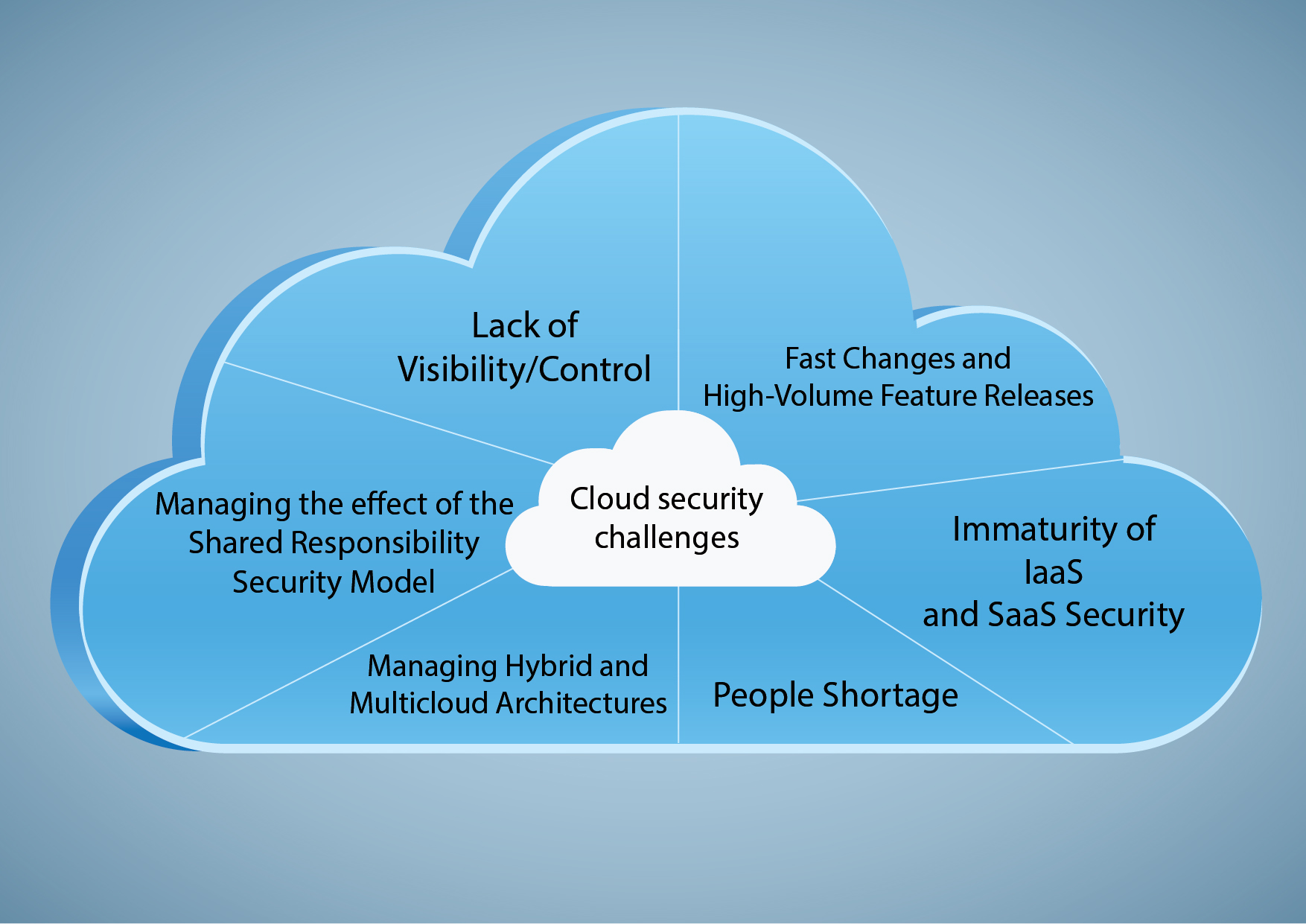
One of the advantages of using cloud-based technologies is that the user does not have to manage the resources required to keep it working (For example, servers). Yet, handling off the responsibility for managing the up-to-date software, platform, or computing resource can result in less visibility and control over that asset.
The Cloud Service Provider (CSP) is responsible for protecting its network and infrastructure. Their SecOps team observes the computing, storage, and network hardware composing the cloud platform. As a result, the client is responsible for their data and application security, such as patching and access control problems that arise with working in the cloud.
CSPs often introduce new features and solutions to attract new customers and keep current customers from defecting. Few of these changes can have massive effects on SecOps.
CSPs make multiple security tools available in their cloud platforms, including cloud-based IDSs and virtual web application firewalls. However, these CSP security offerings subject to be incomplete compared to their conventional data center counterparts. This gap makes SecOps teams having to install and manage their tools.
Few enterprises are 100% in the public cloud. Many companies have data across public, on-premises, and private cloud architectures, and others have applications and data that bridge AWS, Azure, and Google cloud. Such hybrid cloud architecture builds up tricky security dynamic for SecOps to track. It requires many overlapping and redundant systems for various cloud instances. This increases the possibilities of human error and the need for automation further.
A shortage of proficient, available, and affordable SecOps workforce is becoming an increasingly urgent issue for almost every security enterprise that’s working in the cloud.
The growing use of sanctioned and unsanctioned cloud-based applications with security programs for the cloud that are often less mature than present on-premise initiatives has led to a significant loss of corporate data. The main contributors to data loss included violations of security policy, the implications of employees using their own devices, and the lack of adequate access controls.
Enterprises figured out massive enhancements needed to protect sensitive data regardless of location. And 40% of respondents expect cybersecurity spending to increase considerably.
According to McAfee, the organization’s use of cloud solutions grown by 50% between January and April 2020. Simultaneously, external threat actors increased by 630%. The report also focuses on cloud-native security considerations as critical for company workloads operating in the cloud. In response, some tasks should be automated, such as:
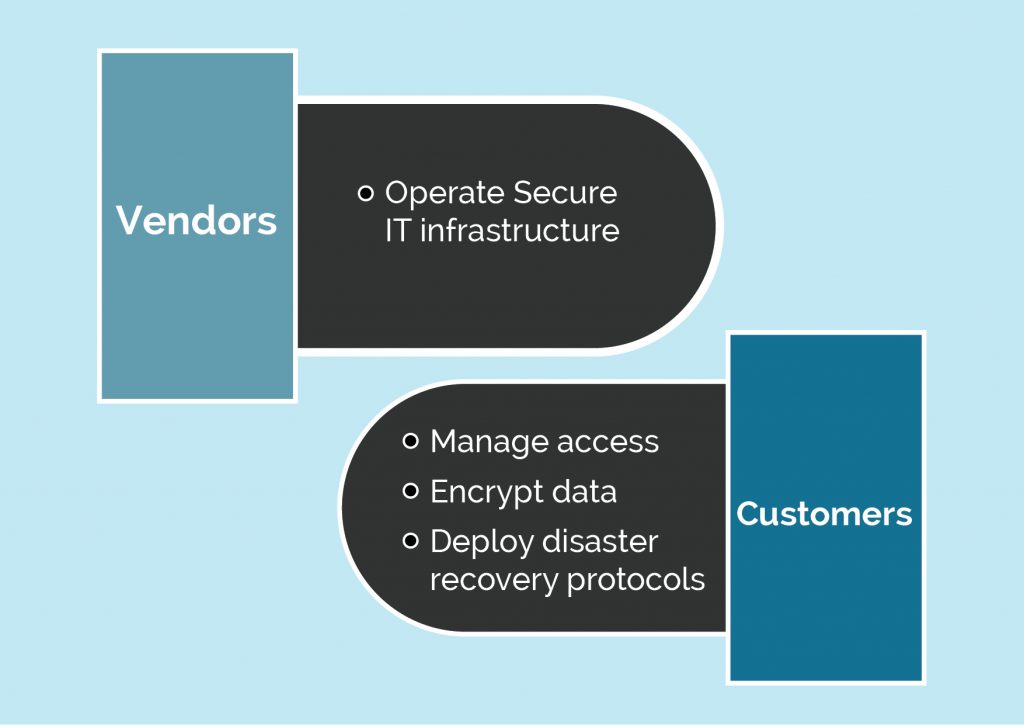
Prediction: Enterprises must carefully realize and follow the shared cloud security responsibility model: vendors are accountable for operating a protected IT infrastructure. Customers are responsible for managing encryption, access, and disaster recovery protocols.
The capability to obtain greater operational efficiencies by unifying security policies across on-premises and cloud-resident data regulate compliance.
Ensuring data confidentiality and data security in the cloud
Ensuring data confidentiality is complex for both maintaining trust in your enterprise and meeting compliance needs. The high-profile breaches consistently in the news highlight the high cost of data security problems. In general, national and international guidelines that include the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR) need enterprises to ensure the security and privacy of various critical data types impose including stiff fines for compliance failures.
The most massive threat to data confidentiality is the capability for unauthorized access to sensitive data. There are two methods for dealing with this risk, which can be used together or individually:
Discover and categorize your data. To ensure the sensitive data is stored only in protected locations and accessible only by authorized users. Also, you need to know which of your information is exposed and the place of the data. Knowing which data needs protection will help you set priorities and apply multiple security controls based on classification outcomes.
Use data masking. This approach involves securing sensitive data by encapsulating it with characters or other data. Data can be hidden in real-time or its original location when requested by an application or a user.
One of the secure and most common data masking approaches is encryption, making it impossible for unauthorized parties to view or realize stored or shared data. Encryption can be asymmetric, which needs a public key and a private key, or symmetric, which utilizes just one private key for encryption and decryption. Actual encryption key management is involved; in general, you must create policies that guarantee only trusted people can access them. Cloud encryption solutions help you to prevent prying eyes from accessing your secured data.
To summarize, while cloud migration can drive your business growth, any compromise in cloud security can push you down. Passwordless methods are popular nowadays, and they ensure safety, as they are used to hold out against cybercriminals, who try to hack passwords for accessing cloud-based apps. One single method or technology won’t protect your cloud data, but a cluster of multiple technologies can surely complement one another. Enterprises invest heavily in the cloud security workforce, i.e., towards skills, competencies, and governance tools. An organization’s own IT department’s role is indispensable as security and privacy have always been two major checkpoints in adopting cloud.

With over 18+ years of experience in Software design and development, Tahir's expertise lies in designing and developing high-quality products and solutions spanning multiple domains. He is versatile and always eager to tackle new problems by constantly researching and deploying emerging techniques, technologies, and applications.
Have a reputable and trustable managed security services provider assess your data storage and security requirements today.
One reply on “Cloud Data Security Trends”
Knowledgeable information