Ensure data security with data classification to protect your organization’s sensitive data
Data protection is at risk during this pandemic and likely a target of malicious behavior or intrusive cybercriminals. Data classification offers one of the best ways for enterprises to define and assign relative values to their data and ensures data security The process of data classification enables you to categorize your stored data by sensitivity and business effect, so you realize the risks connected with the data. Instead of handling all data the same way, you can manage your data in ways that reflect its value to your business.
Data exists in three primary states, i.e., at rest, in process, and transit. All three states need distinctive technical solutions for data classification. Also, you should apply the same standards of data classification for each. The confidential data needs to stay confidential when at rest, in process, and transit.
Data can be Structured or Unstructured
General classification processes for structured data found in spreadsheets and databases are less complicated and time-consuming to manage. Unstructured data that include documents, source code, and email are more complex than structured data. Usually, companies have more unstructured data than structured data.
At Sun Technologies, we believe that one of the best data protection aspects is the right data classification. If you know what and where your critical data is, you would secure it reasonably and save your company from possible heavy penalties and compliance breaches. A little while back, we have seen the GDPR compliance violation at H&M with the largest financial penalty following illegal employee surveillance. The company could have avoided the threat if it had followed privacy compliance policies and addressed the data within data classification plans.
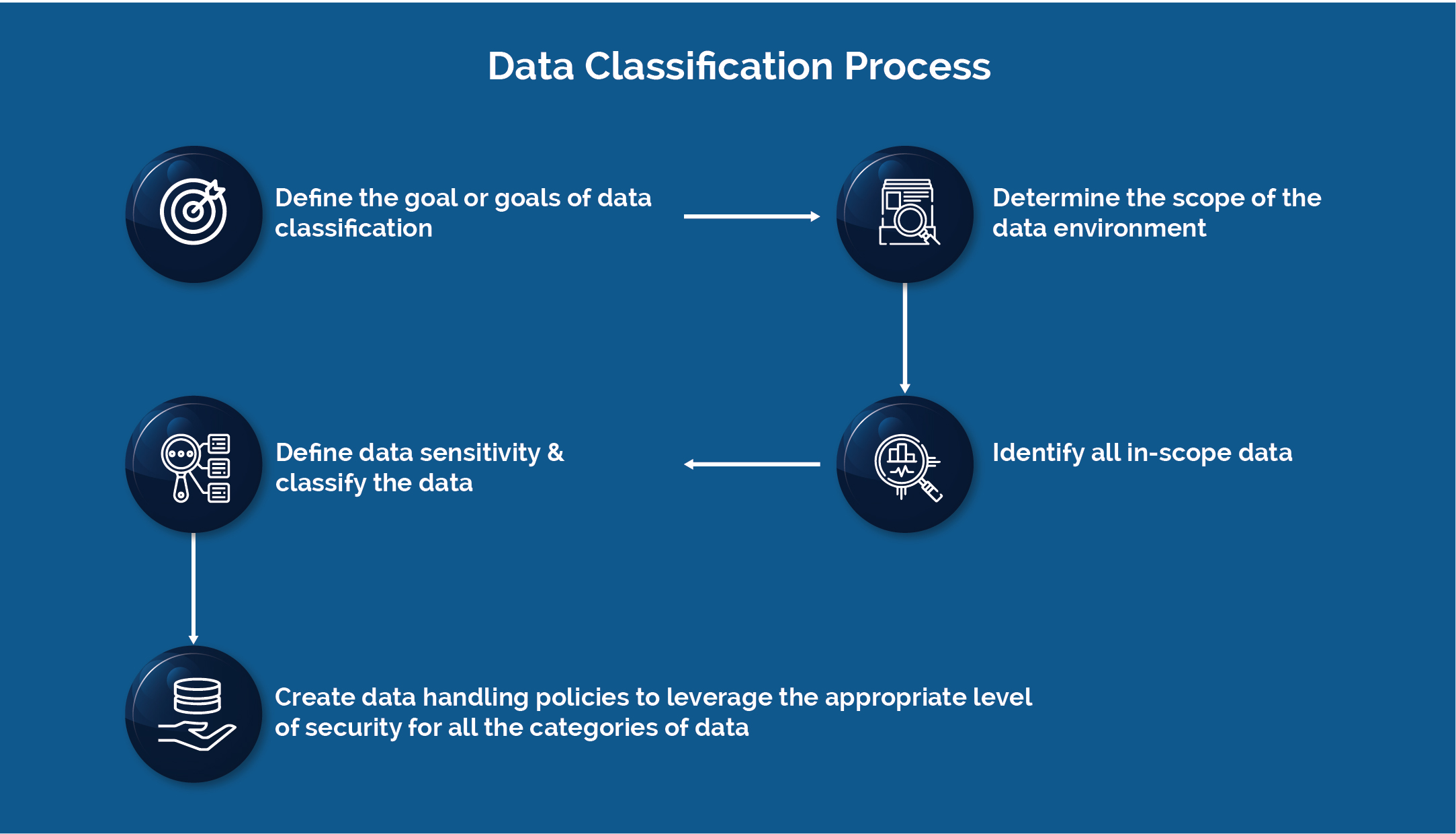
Process of Data Classification
- Establish a data classification strategy, including goals, workflows, data classification scheme, data owners, and managing data
- Figure out the critical information you store
- Apply tags by labeling data
- Use results to enhance security and compliance
- Data is vigorous, and classification is an ongoing process
Guidelines to Classify the Data
Enterprises can achieve data discovery through various automated tools that are available in the industry. But most importantly, your enterprise should define the classification scheme and criteria initially. At Sun Technologies, we follow the reliable and demonstrated framework to classify, declassify, and secure sensitive data. The following are some of the steps from our extensive framework.
1. Define the business objective
The initial step is to understand the business objectives and evaluate your enterprise’s risk and compliance needs. Then categorize the ranking of risks and a list of initiatives to reduce the risk.
2. Understand the requirements and classify data accordingly
At times, it is challenging to meet the compliance needs to meet the critical business requirements. Thus, a reliable data classification program needs to be developed to classify the data according to its risk and value. We have established a dedicated and demonstrated extensive framework by complying with SOX, NIST, CERT, PCI, PII, HIPAA, and many other regulatory requirements. The scheme is a combination of people, process, innovation, and technology, which will find new data elements, shadow IT, structured and unstructured data. And also, it discovers sensitive data in areas you usually never expect. It will identify the broken process, bad actors, data drift, and declassify the data. With that information, We would suggest implementing a sufficient number of DLP tools to secure data-at-rest, data-in-process, and data-in-transit across the IT industry to deliver comprehensive data security.
3. Categorize, Monitor, Track, and Response
Including a proper incident life cycle management to data classification is vital. It reports the incident occurrences and recommends how to respond to that incident, perform the root cause analysis, etc. Sun Technologies has a fully managed SIEM and SOAR capability, which will get the logs and events from your DLP solutions and associate them with external threat intelligence feeds to give environmental and functional alerts through a dashboard. This enables our SOC team to efficiently detect and resolve attacks of all types by providing compliance status, risk profile and categorized incidents that produce the biggest threat to data.
Benefits of Data Classification
Classifying data helps enterprises ensure regulatory compliance and enhance data security.
Data Security
Classification is an efficient way to safeguard your valuable data. Identify the types of data you store and discover the location of sensitive data, and this makes you to:
- Prioritize your security measures, revamping your security controls based on data sensitivity
- Recognize who can access, change or delete data
- Evaluate risks, such as breaches that impact business, ransomware attack or other threat
Regulatory Compliance
Compliance regulations need enterprises to secure data, such as cardholder information (PCI DSS) or EU residents’ data (GDPR). Classifying data allows you to find the data subject to specific regulations so you can apply them for the required controls and pass audits.
The following defines how data classification can help you meet general compliance standards
- GDPR— Data classification helps you endorse the rights of data subjects, including satisfying data subject access request by restoring the set of documents with information about a given individual.
- HIPAA— Knowing where all health records are stored helps you implement security controls for the right data protection.
- ISO 27001 — Classifying data based on value and sensitivity helps you meet requirements for preventing unauthorized disclosure or modification.
- NIST SP 800-53— Categorizing data helps federal agencies suitably plan and control their IT systems.
- PCI DSS— Data classification allows you to find and protect consumer financial information used in payment card

Vaidyanathan Ganesa Sankaran
Vaidy is an experienced lead Solutions Architect heading sales and project delivery for Cloud (AWS, Azure), DevOps and legacy Modernization projects with a demonstrated history of working in the information technology and services industry. He is a strong engineering professional with a Master of Science (MS) focused in Computer Software Engineering from BITS Pilani. He has the capability to manage bigger teams and generate revenue through new Sales and Account Mining.
Recent Posts
Looking for Data Security Services?
We help you to discover best practices and maximize ROI in data security and protection solutions.




