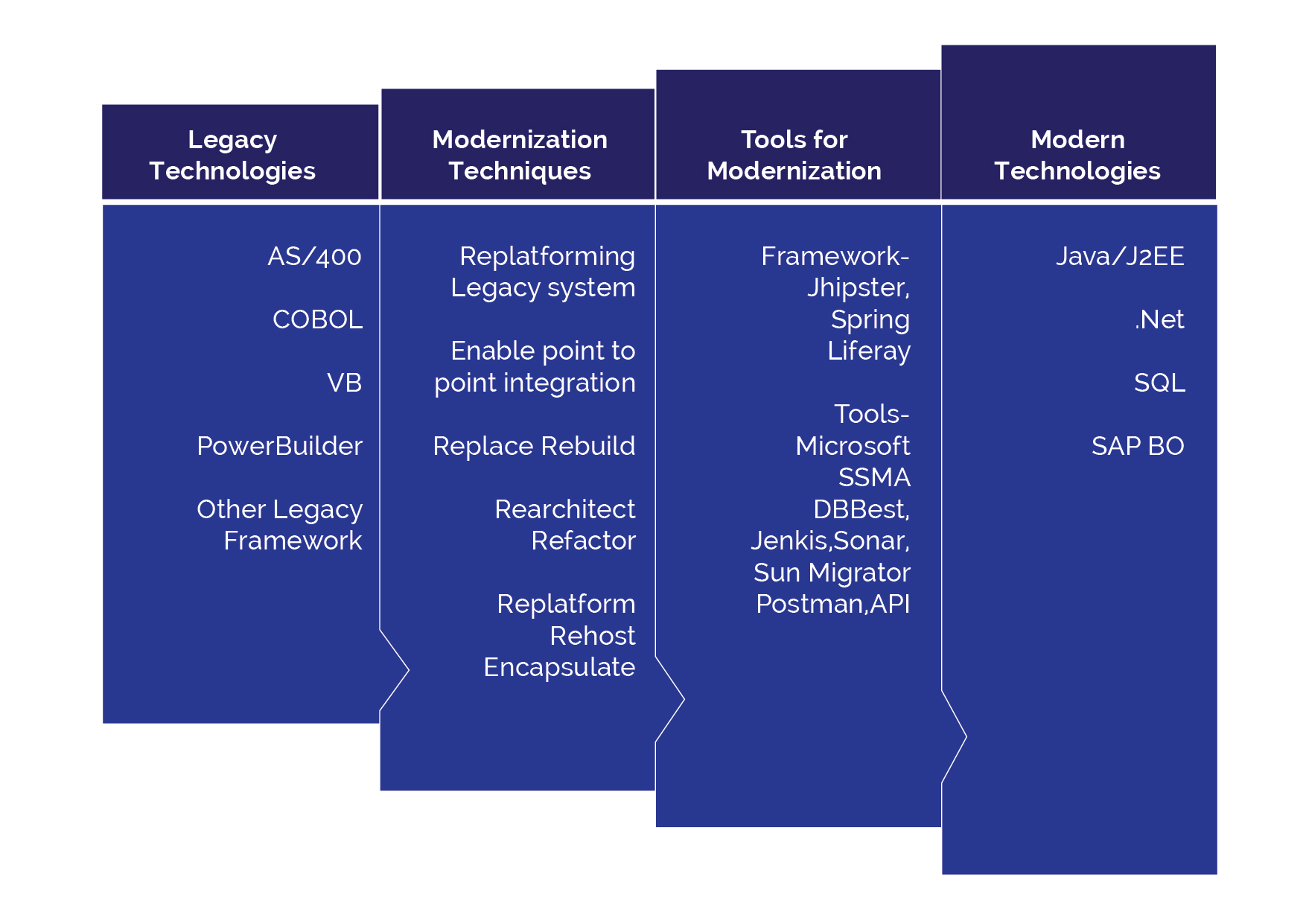
Automation plays a vital role in successful Continuous Integration (CI) and Continuous Delivery (CD). The scripts, plugins, and other automation tools help systemize the deployment processes and reduce software delivery errors. As a result, applications are maintained and delivered securely and quickly than ever.
Automation should cover a complete CICD life cycle to include the deployment and post-deployment phases of software delivery. Also, Security plays a significant role in CI/CD. Automation is needed to verify the security controls, monitoring, and remediation during the complete process, from initial code uploads to the applications’ deployment and distribution. Automation is also needed for relying on CI/CD to simplify the user experience when applications are deployed.
Build better products using CI/CD pipelines
CICD is not restricted to just automation of tasks to reduce human error; it’s beyond the automation. It makes you deliver new solutions into users’ hands as rapidly and cost-effectively as possible. Sun Technologies CICD DevOps pipelines aims at removing manual errors and provide regular feedbacks that allows fast iterations focusing product release and build better.
Advantages of CICD at enterprise level:
CI/CD pipelines streamlines release processes over projects and minimize the chances of introducing bugs.
A CICD pipeline can monitor complete process from commit to production in one screen. One can navigate across various phases and identify inefficiencies.
CICD helps product management to improve user impact. Developers deploy new code that results in a faster development and better products.
CI/CD helps product management to improve user impact. Developers deploy new code that results in a better development team and better products.
Challenges enterprises face while deploying multiple projects
Each project requires different deployment pipelines
Each project requires an individual deployment pipeline since the deployment of multiple projects happens in the same prod environment. This leads to numerous deployment pipelines.
Manual effort required to change the configurations for multiple environments
Each project has its own configurations applied to various environments (DEV, UAT, PRE-PROD, PROD). This requires manual effort to change the configurations for each environment. For example, Configurations value such as endpoint URL for third party application, certificate files, or account credentials for each environment is different.
Sun Technologies help you overcome these challenges by taking efficient actions in the DevOps pipeline with our DevOps Services.
Tools to simplify your development Process
While developers enjoy writing and managing codes, dependencies can quickly become complicated when you’re focusing on the continuous growth of your codebase and features. At Sun Technologies, we help reduce the developer’s work using continuous integration tools.
Sun Technologies has deep expertise on below toolsets to strengthen a DevOps Pipeline:

How Sun Technologies automates build and deployment for multiple applications effectively?
Sun Technologies deployed multiple projects using a single deploy pipeline. With our ideal workflow, teams get faster builds, shorter feedback cycles, and simplified pipeline maintenance. We also provide end-to-end solutions for CICD ranging in a variety of complexity.
Our Custom Automation workflow involves collecting various modules from different dependant teams and deploy them in a single environment. With Containerization being an automated step within the DevOps pipeline, these images are managed in Nexus or JFrog artifactor. Sun Technologies has a customized home-grown tool, “Sun Vault,” which helps store passwords / Keys in an encrypted format. This helps in avoiding hard coding of passwords within the DevOps pipeline, thereby ensuring security.
Conclusion
To summarize, most of the CICD complexities are related to poor implementation and inadequate practices. Proper evaluation of CICD requirements, selecting the right tools, and trained experts will lead to a successful CICD implementation. As an enterprise, the organization could concentrate more on shipping features than managing operations and engaging in repetitive tasks. Hence, CICD pipelines help in building and enhancing the applications with a shorter time-to-market, improved customer satisfaction, and better user experience. Automation in DevOps pipeline simplifies the processes and helps in building better products.
IntelliSWAUT, the scriptless test automation tool, is an all-in-one solution that covers all your test automation needs. With IntelliSWAUT, enterprises can now optimize and enhance their Quality Assurance process and excel their ci/cd pipelines to improve the development process and fine-tune their final product.
Read what makes IntelliSWAUT the perfect fit for projects with tight deadlines and dynamic scope.
Equip your test automation and ci/cd pipeline with IntelliSWAUT

Vaidyanathan Ganesa Sankaran
Vaidy is an experienced lead Solutions Architect heading sales and project delivery for Cloud (AWS, Azure), DevOps and legacy Modernization projects with a demonstrated history of working in the information technology and services industry. He is a strong engineering professional with a Master of Science (MS) focused in Computer Software Engineering from BITS Pilani. He has the capability to manage bigger teams and generate revenue through new Sales and Account Mining.
Recent Posts
Looking for an automated deployment process?
We help simplify your project’s deployment process and build efficient products .